When researching about the _doClick related concepts, I found a hack that might possibly be a serializaied representation of the memory segment where a formula command will be stored in a server.
This sounds funny and frightening to me - "Yin and Yang" concept, if I am not wrong.
Well as usual try the following ridiculous stuff and tell me that I am not crazy.
1. Create/open a form in Lotus Notes
2. Create a button and put some formula code inside it as illustrated in the following screen shot.
3. Now navigate to the HTML tab of the button properties dialog and simply add "<>" in the 'Other' field as illustrated in the previous screen shot .
4. Now preview the form in browser and you will be able to see some thing like this
Discussion points in few forums say that these numbers are memory segment representation sort of stuffs in the server with the domino uses via "_click" field in post data or a &click argument in a url to trigger and execute these formula commands.
Man this stuff is crazy.
Share your thoughts and find that its getting better every day. This work of mine helps me realize that.
Showing posts with label Hacks. Show all posts
Showing posts with label Hacks. Show all posts
Thursday, January 3, 2013
_doClick in Lotus Notes - A javascript refresh trigger other than window.reload
This was a strange stuff that I have never encountered before. This is a nice stuff that one can use to screw your lotus domino based web pages with as well. Hope there are not too many hackers around.
I stumbled upon this when I had to avoid a page refresh that was triggered due to selection of the property named "Refresh fields on keyword change" for a combobox field type in the lotus notes form.
It was like there were no ways to impose a partial refresh of web page segments like the ones available with XPages. Eventually search for a desparate hack went in vain but I was able to discover the existence of this particular hack.
Hope this helps some one though I did not have any use for the same. Following is what I am speaking about.
1. Create a form. Include a dropdown "combo" field in it. Give it some options and select the property "Refresh fields on keyword change".
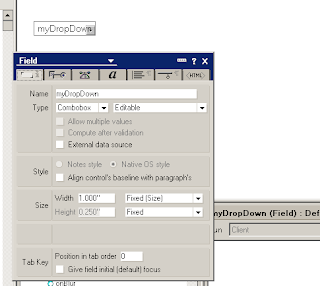
2. The property selection I am speaking about is illustrated as follows
5. Now preview the form on the web. Nothing big right. You see 2 simple fields just as expected
6. And if you change a value in the dropdown, you page will be refreshed because of the associated option "Refresh fields on keyword change". So eventually, you will be able to see a new time that is computed and displayed on the webpage
7. Now go back to the designer and uncheck the option "Refresh fields on keyword change" in your combobox properties window
8. And add the following code in the onchange event of the dropdown box.
_doClick('$Refresh', this, '_self', '#_RefreshKW',"myDropDown")
9. Now save and preview your webpage again and try changing the values in the dropdown again. You will be able to recognize that the page behaves in a simialr way and it is no different from the property selection on the dropdown field.
10. Interesting right.
Now my worry is I guess, I will be able to perform a few hacks with this. So more to think about when developing webpages in future :(
Hope this helps :)
I stumbled upon this when I had to avoid a page refresh that was triggered due to selection of the property named "Refresh fields on keyword change" for a combobox field type in the lotus notes form.
It was like there were no ways to impose a partial refresh of web page segments like the ones available with XPages. Eventually search for a desparate hack went in vain but I was able to discover the existence of this particular hack.
Hope this helps some one though I did not have any use for the same. Following is what I am speaking about.
1. Create a form. Include a dropdown "combo" field in it. Give it some options and select the property "Refresh fields on keyword change".

2. The property selection I am speaking about is illustrated as follows
3. Put a date time field near by the combo box and ensure that it displays time upto seconds at any point of its display
5. Now preview the form on the web. Nothing big right. You see 2 simple fields just as expected
6. And if you change a value in the dropdown, you page will be refreshed because of the associated option "Refresh fields on keyword change". So eventually, you will be able to see a new time that is computed and displayed on the webpage
7. Now go back to the designer and uncheck the option "Refresh fields on keyword change" in your combobox properties window
8. And add the following code in the onchange event of the dropdown box.
_doClick('$Refresh', this, '_self', '#_RefreshKW',"myDropDown")
9. Now save and preview your webpage again and try changing the values in the dropdown again. You will be able to recognize that the page behaves in a simialr way and it is no different from the property selection on the dropdown field.
10. Interesting right.
Now my worry is I guess, I will be able to perform a few hacks with this. So more to think about when developing webpages in future :(
Hope this helps :)
Labels:
Hacks,
Javascript,
Lotus Notes
Thursday, November 22, 2012
XSS - Possible measures
I understand that there are some tools like Nessus and Nikto that would help detect such attacks. I have no idea about them though. Just came across these stuffs and hence though of sharing the same.
Following is a shame less copy and paste. Again just wanted to share what I read.
Following is a shame less copy and paste. Again just wanted to share what I read.
How to Protect Yourself
The primary defenses against XSS are described in the OWASP XSS Prevention Cheat Sheet.
Also, it's crucial that you turn off HTTP TRACE support on all webservers. An attacker can steal cookie data via Javascript even when document.cookie is disabled or not supported on the client. This attack is mounted when a user posts a malicious script to a forum so when another user clicks the link, an asynchronous HTTP Trace call is triggered which collects the user's cookie information from the server, and then sends it over to another malicious server that collects the cookie information so the attacker can mount a session hijack attack. This is easily mitigated by removing support for HTTP TRACE on all webservers.
The OWASP ESAPI project has produced a set of reusable security components in several languages, including validation and escaping routines to prevent parameter tampering and the injection of XSS attacks. In addition, the OWASP WebGoat Project training application has lessons on Cross-Site Scripting and data encoding.
And I guess you can get more ideas on the possible ways by which you can be exploited in http://ha.ckers.org/xss.html.
Hope this helps :)
XSS Cross-site scripting makes me worry
The concept of cross site scripting rang a bell inside me a long time ago. I was kind of wary about it and I even learnt to perform it. Hey I am not a hacker, dont start getting ideas already. Its just that I am curious and feel very happy to experiment stuffs the safe way as most of us prefer to do. Recently I came across a nice post about it in https://www.owasp.org/index.php/Cross-site_Scripting_(XSS).
It was very informative and very useful. I am getting newer ideas even when I am typing this one down. All stuffs posted in the site are basic and clean, but opens up my mind to a lot of potentially harzardous methods, if employed by some one against my sites, would be a massacre.
By my thoughts some of the stuffs that bothers me about how XSS may affect us are
1.
<html>
<body>
<? php
print "Not found: " . urldecode($_SERVER["REQUEST_URI"]);
?>
</body>
</html>
2.
http://testsite.test/<script>alert("TEST");</script>
3.<%...
Statement stmt = conn.createStatement();
ResultSet rs = stmt.executeQuery("select * from emp where id="+eid);
if (rs != null) {
rs.next();
String name = rs.getString("name");
%>
Employee Name: <%= name %>
where name can be an XSS Hack
You can steal user session cookie etc.. and a lot more of such examples can be made
Most of the times when I am into serious mind wrecking program issues, all I would need was one loop hole, however small it may be, and I would fix the issues. I will just get what ever I want out of it.
All I did here was 10 minutes of thinking about what can I do with XSS. And I already got a lot of options.
Worst case, if I could understand a browser, which I definelty can if I spend a couple of months may be, I my self can do idiotic stuffs. So what can a full time hacker be capable of. Hope I dont get a cyber attack. This is scary
Tuesday, September 27, 2011
Can a field name exceed 32 characters
Well It just happened on the go. I know the name of a field cant be bigger that 32 characters in lenght. I got a bit curious to see if I can break it. But the designer did not allow me to do it.
So as always 2 over come this I had my step2 - the Lotus Script.
I just created a document Item whose name is 52 characters in length. And yes it can exceed. But I havent tested its limits yet. Following are screen shots that would best describe what I am speaking about
I hope we can over come the designer limitation as well using DXL. Hope this is interesting and useful :)
So as always 2 over come this I had my step2 - the Lotus Script.
I just created a document Item whose name is 52 characters in length. And yes it can exceed. But I havent tested its limits yet. Following are screen shots that would best describe what I am speaking about
I hope we can over come the designer limitation as well using DXL. Hope this is interesting and useful :)
Labels:
Hacks,
Lotus Notes,
Lotusscript
Subscribe to:
Posts (Atom)










